Productivity Tools
September 9, 2025
Webhooks Explained: What They Are and How They Power Real-Time Automation
If you’ve ever wished your tools could “tap you on the shoulder” the moment something important happens-like a new payment, sign‑up, or support ticket webhooks are how that magic happens. They’re the connective tissue of modern SaaS, quietly delivering event data from one application to another in near real time. Yet many teams still treat webhooks like a black box: they enable them, hope for the best, and scramble when deliveries fail.
This guide demystifies the topic. We’ll explain what a webhook is, how it differs from an API, the anatomy of a secure event delivery, and the patterns you can copy to make your integrations resilient. You’ll also get industry‑grade best practices, testing tips, and concrete examples you can use today. By the end, you’ll know exactly how to use webhooks to power reliable, event‑driven automation.
What Is a Webhook?
A webhook is a simple mechanism for delivering event data from one system to another without polling. When an event occurs (say, an invoice is paid), the source system makes an HTTP POST request to a URL you control (your webhook endpoint). That request contains a payload (commonly JSON) describing the event. Your service validates the request, processes the data, and responds with a 2xx status code to acknowledge receipt.
Unlike traditional request/response patterns where your app repeatedly asks another service “did anything happen yet?”, webhooks push data at the moment something changes. The result is lower latency, fewer wasted requests, and a smoother user experience.
Polling vs Webhooks vs WebSockets
| Method | Who initiates | Connection model | Typical latency | Strengths | Trade-offs |
|---|---|---|---|---|---|
| Polling (API) | Client | Repeated requests | Higher (seconds–minutes) | Simple, firewall-friendly | Wasteful requests; delays |
| Webhooks | Provider | One-off HTTP POST | Low (sub-second–seconds) | Real-time-ish, scalable | One-way; must expose endpoint & verify |
| WebSockets | Either | Persistent bi-directional | Very low (ms) | Live streams, chat, dashboards | Connection management; stateful scaling |
How Webhooks Work (Step by Step)
- Register your endpoint – In the provider’s settings, you specify your webhook and the events you care about (e.g., invoice.paid).
- Provider observes events – The provider’s system monitors for the selected events.
- Delivery attempt – On each event, the provider sends an HTTP POST with headers (often including a signature) and a JSON body.
- Validate & queue – Your endpoint verifies the signature, enqueues the payload for background processing, and immediately returns 200 OK.
- Process asynchronously – A worker consumes the queue job, performs business logic (update DB, notify users, trigger downstream automations), and logs the result.
- Retries on failure – If your endpoint is down or slow, reputable providers retry with backoff. Your system should be idempotent so replays don’t cause duplicates.
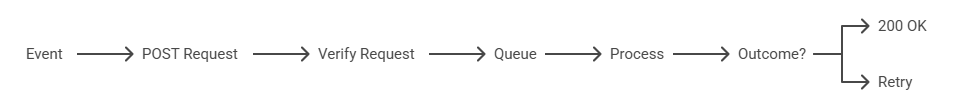
How a webhook moves from an event to delivery, verification, queuing, processing, and either a 200 OK acknowledgment or a retry
Anatomy of a Robust Webhook
Designing a dependable consumer starts with a clear contract between sender and receiver.
Endpoint URL
Use a dedicated path per provider (e.g., /webhooks/stripe, /webhooks/github). This keeps logic isolated, simplifies rotation of secrets, and improves observability.
Method, Headers & Content Type
Most deliveries are HTTP POST with Content‑Type: application/json. Providers often include timestamped signature headers (e.g., HMAC) you can verify with a shared secret.
Payload Shape
Payloads typically include a top-level event type, unique event ID, creation timestamp,
and a data object containing the subject (payment, issue, message).
Example:
{
"id": "evt_01J8…",
"type": "invoice.paid",
"created": 1725302400,
"data": {
"object": {
"invoice_id": "inv_123",
"amount_paid": 4999,
"currency": "USD"
}
}
}
Verification & Authentication
Always validate that the request came from the provider. Common methods include HMAC signatures (compute a hash of the raw body with your secret and compare) and IP allowlists published by the provider. Reject requests that fail verification.
Idempotency & Ordering
Deliveries can be retried or arrive out of order. Use the event’s unique ID to deduplicate and store a processed‑at record. If order matters (e.g., customer.created before invoice.paid), buffer short‑term or reconcile via the provider’s API.
Response Codes
Acknowledge quickly with 2xx. Use 4xx for permanent errors (bad signature) and 5xx for transient failures (DB down) so providers know whether to retry.
Webhooks vs. REST APIs: When to Use Which
Think of webhooks as notifications and APIs as orchestration. Webhooks tell you that something happened; APIs let you ask for details or change state. The most reliable integrations pair them: accept a webhook, verify it, then fetch the current source of truth via API before writing to your database. This guards against stale payloads and race conditions.
A good rule of thumb: if the next action must occur immediately when an event fires, favor a webhook; if a human or UI needs data on demand, call the API.
Use‑Case Playbooks (By Team & Industry)
Product & Growth – Trigger onboarding emails the instant a trial starts; nudge users when usage milestones are hit; sync lifecycle events to your CRM without cron jobs.
Finance & Billing – Update invoices as soon as payments settle; alert on failed charges; post ledger entries to the accounting system in real time.
Support & Success – Create tickets automatically when customers submit forms; escalate high‑severity events to on‑call channels; close the loop when issues resolve.
Engineering & DevOps – Kick off CI/CD on a push; auto create incidents on error spikes; fan out deploy notifications to Slack and StatusPage.
E‑commerce & Logistics – Notify shoppers on shipment scans; update stock counts when returns are received; trigger reorder workflows.
Education & Healthcare – Deliver grade posted alerts; push intake forms into EMRs (with strict security).
Each scenario benefits from the same pattern: verify → queue → process → reconcile.
Security & Reliability Best Practices
- – Enforce HTTPS and HSTS; never accept plaintext HTTP for webhook intake.
- – Verify signatures (HMAC with provider secret) against the raw request body and a fresh timestamp window.
- – Respond fast (≤ 2–3s) with 2xx; do heavy work off the request thread via a queue/worker.
- – Make handlers idempotent using event IDs; dedupe before side effects.
- – Implement retry/backoff on your side when calling downstream services; expect provider retries too.
- – Capture structured logs & metrics (latency, success rate, error codes); ship to your observability stack.
- – Protect endpoints with allowlists, WAF rules, and rate limits; rotate secrets regularly.
- – Reconcile with source APIs for critical writes to counter out‑of‑order or partial deliveries.
- – Version your consumers and support multiple payload shapes during migrations.
Implementation Blueprint: Build Your First Consumer
Below is a minimal, production-leaning approach. The language is Node.js/Express, but the pattern is universal.
Show code
import express from "express";
import crypto from "crypto";
const app = express();
// Capture raw body for signature verification
app.use(express.raw({ type: "application/json" }));
const SECRET = process.env.WEBHOOK_SECRET;
function verifySignature(rawBody, signature, timestamp) {
const payload = `${timestamp}.${rawBody}`;
const expected = crypto
.createHmac("sha256", SECRET)
.update(payload)
.digest("hex");
return crypto.timingSafeEqual(Buffer.from(signature), Buffer.from(expected));
}
app.post("/webhooks/provider", async (req, res) => {
const sig = req.header("X-Provider-Signature");
const ts = req.header("X-Provider-Timestamp");
const raw = req.body.toString("utf8");
if (!sig || !ts || !verifySignature(raw, sig, ts)) {
return res.status(400).send("Invalid signature");
}
const event = JSON.parse(raw);
// Idempotency guard (pseudo-code)
// if (await hasSeen(event.id)) return res.sendStatus(200);
// await markSeen(event.id);
// Queue for async processing (pseudo-code)
// await queue.publish("events", event);
return res.sendStatus(200);
});
app.listen(3000, () => console.log("Webhook consumer listening on 3000"));From here, your worker consumes the queue and performs business logic (DB writes, API calls, notifications). This separation keeps the intake endpoint snappy and resilient.
Testing, Tools & Troubleshooting
Local development is easier than you think. Tunnels like ngrok or Cloudflare Tunnel expose your localhost securely
For one‑off inspections, tools like webhook.site or RequestBin show headers and bodies exactly as sent.
When debugging, start with three questions: Did the provider attempt delivery? (check their dashboard), Did our endpoint acknowledge? (2xx in logs), and Did our worker finish the job? (trace IDs in logs/metrics). Most issues fall into one of: signature mismatch (wrong secret or timestamp skew), slow processing (do it off thread), or idempotency gaps (double charges, duplicate emails). Address those and your success rate climbs fast.
Conclusion
Webhooks are the simplest way to make products feel instantaneous. By combining a verified intake endpoint, idempotent processing, and clear observability, you can trust every event to land and every action to happen once and only once. Treat webhooks as part of your core platform, not a side quest: document your contracts, test with real payloads, and reconcile against source APIs for critical paths. Do this and you’ll unlock a durable, real time integration layer that scales with your business.
Next steps: identify one high‑impact event (e.g., payment succeeded), draw the lifecycle, implement the verified intake + queue pattern, and ship. Measure delivery rate, latency, and failure causes in your dashboard; iterate weekly until it’s boring-in the best way.
FAQ
- What is a webhook in simple terms?
A push notification over HTTP-when something happens, the provider POSTs a signed JSON payload to your URL. - How do webhooks work?
You register a webhook URL. On each event, the provider sends JSON; you verify signature + timestamp, return 2xx fast, and process asynchronously. - What is a webhook URL?
A unique HTTPS endpoint (e.g., /webhooks/provider) that receives events. Treat it like a secret and validate every request. - Webhook vs API-what’s the difference?
APIs are request/response you call; webhooks are event-driven pushes from the provider. Use both: webhooks to get notified, APIs to fetch/change data. - How do I create a webhook?
Build a POST endpoint, store a secret, verify HMAC + timestamp, ACK fast, enqueue for async work, and enforce idempotency. - How do I secure webhooks?
Use HTTPS, verify HMAC with timing safe compare, validate timestamp skew, rotate secrets, and optionally IP-allowlist provider ranges.
Like what you see? Share with a friend.
Itay Guttman
Co-founder & CEO at Engini.io
With 11 years in SaaS, I've built MillionVerifier and SAAS First. Passionate about SaaS, data, and AI. Let's connect if you share the same drive for success!
Share with your community




.png)
Comments